 |
hacking for the fun of it |

Name: Keykeriki
Type: Hardware and Software
Slides:keykeriki_ph7d9.pdf (Our slides
from ph-neutral7d9)
Hardware:keykeriki-hw-0.6.tar.gz
(Eagle files, partlists, build howto)
Software:keykeriki-release-0.5.2.tar.gz
(Software & documentation)
Documentation: See folder "docs" within the download
package
License: OpenSource, free for non-commercial use, commercial
usage needs special permission
Contact: hardhack@remote-exploit.org
Description: Now, 1.5 years after releasing our
whitepaper "27Mhz Wireless Keyboard Analysis Report" about wireless
keyboard insecurities, we are proud to present the universal
wireless keyboard sniffer: Keykeriki. This opensource hardware and
software project enables every person to verify the security level
of their own keyboard transmissions, and/or demonstrate the
sniffing attacks (for educational purpose only). The hardware
itself is designed to be small and versatile, it can be extended to
currently undetected/unknown keyboard traffic, and/or hardware
extensions, for example, a repeating module or amplifier
Unfortunately we are unable to deliver pre-made PCBs but still
have most components, just drop us an email if you need
help.
Why is there a rooster in the logo for a security
device?
Kikeriki is the scream of a rooster (English:
cock-a-doodle-doo). And because the phonetic sound is very
similar to the word "Key" the name popped up. Funny, heh?
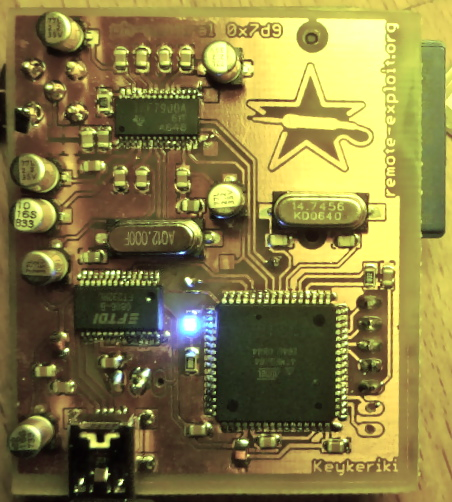
About the hardware: Keykeriki is build around the Texas Instruments TRF7900 chip controlled by an ATMEL ATMEGA 8-bit microcontroller. For logging abilities, an SDCard interface is built into the board layout, as well as an additional USART channel for future hardware extensions, that we'd like to call "backpacks". The whole board can be powered directly via the USB bus or a stable 5V power source. Keykeriki is not USB certified :-).When connected to a USB port, one can use either a decent terminal application or the keyctrl software which is part of included in the software package of this project. One can download all the schematics in Eagle and PDF format as part of the projects software package. The following interfaces are available on the board:
About the Software: Because of the flexible hardware
design, most features are built within software. We wanted to
provide more than just decoding of the collected data in this
initial release, and we have. Please see the following feature
list:
About Backpacks: Keykeriki uses one of the ATMEGA's
USART's for interfacing with external hardware extensions. Those
"Backpacks" add additional functionality. We are not finished with
the design for them, but we are working on the following extensions
so far:
Video: An early prototype LCD backpack in
action
Don't miss our next generation Keykeriki v2 hardware release which is 2.4GHz capable.